I don’t want to be your 'Baby Reindeer': Here's how you can protect yourself from cyberstalkers
It was bound to happen.
After the Netflix comedy drama Baby Reindeer became a global hit show on the streaming giant with a record 60 million views and counting, the Internet did what it does best and tracked down the most likely real-life inspiration for the character Martha Scott, the stalker who was obsessed with Donny Dunn, series creator and writer Richard Gadd’s fictionalized version of himself.
Real-life Scottish lawyer Fiona Harvey claimed to be the person whom Martha was most likely based on. And then things spun out of definite control.
For one, Deadline reported that Netflix’s UK representatives were prompted to appear at a hearing in British Parliament last May 8, with the streamer’s public policy director arguing that they took “every reasonable precaution in disguising the real-life identities of the people involved in that story.”

More recently though, Harvey appeared on the famous UK news talk show Piers Morgan Uncensored where she openly criticized the series as “obscene and defamatory,” threatening to sue both Gadd and Netflix. Harvey claimed that she was the real victim in this scenario with Gadd as the real stalker.
It’s all been way too much controversy for creator Gadd, who never thought his series would make it beyond being a cult hit but is now a veritable overnight success. “I really believed in this show,” he said in an interview with The Daily Record, according to Deadline. “But it really felt like one day it went on the platform and the next day there were people camping in my garden.”

Further and more importantly, the series has motivated discussion on threats to online and offline privacy as well as questions regarding the definition of stalking in today’s social media-saturated world.
Baby Reindeer is an excellent show that refuses to look away at the oft caricatured violence and palimpsest of Donny and Martha’s mental and social health problems. It also deals well with sensitive themes that cover harassment and sexual abuse. Most of all, though, it’s a riveting and escalating watch. An utterly bingeable series you can’t take your eyes off of.
So how do you protect yourself if you think you’re getting too much unwanted attention online or are feeling vulnerable, uncomfortable, or even threatened in interactions on social media and beyond?
Social media privacy
Two things that stalkers can readily monitor these days are social media posts and their GPS footprints.
Both of these are easily available, especially if you’ve allowed the stalker to be your friend on Facebook or they’ve followed you on a public Instagram, TikTok, or X account like Donny did for Martha.
Your posts, the comments section, and your interactions are all data points of what you’re doing or where you’ve been (or are). All our posts can now be tagged with locations, easily letting potential stalkers craft a timeline of where you’ve been and on what day, sometimes up to the minute if you’re fond of live broadcast. Creating fake profiles is also an easy way that stalkers can gather your data from afar, with relative safety and anonymity.
Aside from using tools like blocking or unfriending the person, a good policy to have is to be selective with your circle of online friends from the get go.
If you have confirmed someone you don’t know personally or still have misgivings with, Facebook, for one, has privacy tools that can divide your friend list into certain classifications—like marking them as Close Friends, Acquaintances, or Family. A good rule of thumb, albeit one that requires effort, is to set specific posts (especially ones that have geographical tags or geo tags) to be seen by only people you know personally and can trust.
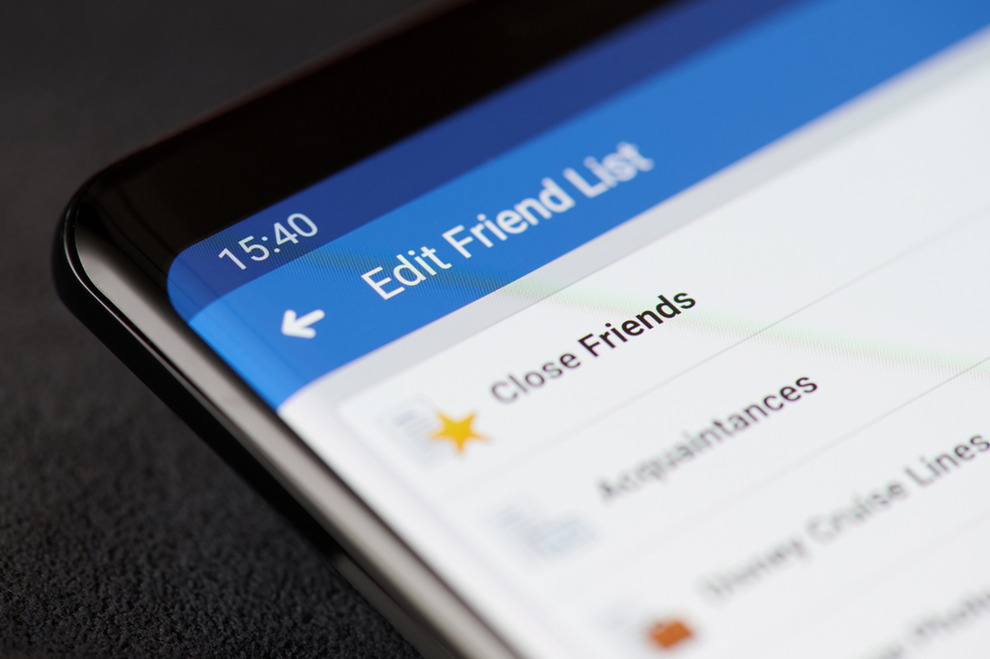
In general, though, the better mindset to prevent social media stalking is to not be in such a vulnerable position at all. Better to have two faces on socials: one for public consumption and another that’s more for private posts.
Ed Geronia, videogames journalist and veteran tech writer, advises the following tips for better control of one’s privacy on social media.
“With your social media accounts, always make sure the default is set to private or friends only,” Geronia told PhilSTAR L!fe. “You can create another account that's public-facing with content that is carefully curated. Check the settings on your devices, health apps, monitors, livestreaming, and Google services as well.”
Even young influencers are finding that dedicated business-facing monetized accounts and emails that aren’t tied to any social media accounts are very useful in maintaining a level of anonymity.
And for when your smartphone or laptop needs to go into the shop for an upgrade or a check-up?
“When sending a device for repair, service, trade-in or reselling, make sure to wipe all the data with a hard or factory reset.”
Aside from that, if you like to routinely use a laptop, putting a thin film of paper or a Post-It strip over your camera when you’re not in a Zoom conference is a good policy overall.

Laws against stalking and bullying
On the show, Martha ended up sending Donny a total of 41,000 emails, 744 tweets, 100 pages of letters, and approximately 350 hours of voicemails.
Cyberbullying and cyberstalking are now considered real risks to life, limb, and reputation. In 2017, the Commission on Human Rights concluded in their investigation that a Grade 8 student from Bago City, Negros Occidental ended his life because of the online bullying he received. There are plenty of other cases of note in the country, too, according to the Cyberbullying Research Center.
“If you are being stalked or abused online, it would be good to cut off any form of contact with that stalker or abuser,” Atty. Melvin Calimag—another veteran tech journalist, and the founder and executive editor of Newsbytes PH—said in an interview with L!fe.
“But if blocking or avoiding him or her isn’t enough, I think it’s still best to report them to the barangay or police and record a blotter. This way, you have ready evidence to present in case you file a case in court.”
If you feel things have gotten out of hand and are receiving anything close to the Martha-threat level that you indeed want the courts to intervene, several local laws are relevant.

To address online harassment, the main legal recourse is the Cybercrime Prevention Act of 2012 (Republic Act No. 10175), which criminalizes offenses such as Cyberlibel and Unlawful or Prohibited Acts.
Second is the Data Privacy Act of 2012 (Republic Act No. 10173). This law will come into play if your harassment or bullying involves any of your devices or accounts getting hacked, even unauthorized collection and dissemination of personal information.
Third is the Anti-Bullying Act of 2013 (Republic Act No. 10627) which is relevant if you are a young person still in school. It mandates that all elementary and secondary schools must adopt policies to address bullying, even if committed through electronic means.
Lastly, there’s the Anti-Violence Against Women and Their Children Act of 2004 (R.A. 9262) which covers “any act or a series of acts committed by any person against a woman who is his wife, former wife, or against a woman with whom the person has or had a sexual or dating relationship.”
The UK has a pretty comprehensive and blanket anti-harassment act that was relevant to Donny on the show when he finally went to the authorities, but only female victims of online bullying in the country have a specific protection law—in line with efforts against our highly prevalent cases of VAWC.
“While there are laws against stalking,” continued Atty. Calimag, “it’s also important to remember that it’s better to protect your personal data so as not to give these stalkers and abusers the chance to do their nefarious activities in the first place.”
Get a VPN
VPN stands for "Virtual Private Network" and can be a great, blanket solution to throw off and even dissuade stalkers who have a good grasp of hacking and tracking tools.

While general smartphone tracking using your IP address, Bluetooth, and GPS services is generally benign, letting apps provide basic services like ride-hailing, food delivery, navigation to the nearest restaurant in your vicinity, it’s easy to see how stalkers can also abuse this kind of tech for their benefit.
A gratis solution is to routinely remember to turn off your location services (the pin icon) on your phone. “Find My Phone” on your iPhone can enable family and friends to track your phone, but so can hackers, exes, and unwanted admirers.
For Android users, signs of being tracked can be performance issues like a quickly depleting battery (your phone’s always too hot). To confirm, go to “Open Settings > Battery and device care.” From there, you can verify by looking at how much battery each app is using. If you see any app you don’t recall installing or it just looks plain suspicious, search online to see if it’s a legit app, otherwise it might be tracking you.
If you have money to throw at the problem though, a VPN app is great all around for privacy, like taking a hike in Doc Martens boots on uneven terrain. Subscription VPNs like Nord, Surfshark, or Express all have tools that encrypt your communications. It also hides your location at another location of your choice, fooling tracking into cataloging you as if you are out of the country. Mine is in Hong Kong by default since it’s near and is the fastest.
A VPN makes you all but invisible to unwanted third parties, even advertisers, hackers, and companies that sell your unique data profile. As a corollary, it also keeps any Martha types at digital arm’s length and off your scent.
Use secure messaging apps
While Meta has been touting the increased security of their Messenger app, it’s worth noting that the popularity of secure messaging apps that specialize in high-level encryption is a good sign that adoption of one (or, better yet, all) of these apps will make your online exchanges less of a hassle to track if things go sideways like what happened to Donny.
An app like Signal has consistently been at the top of tech mag editors’ picks for best secure messaging and it’s a no-brainer.

The reason it’s still the gold standard of this corner of the tech market is you get not only what they call a secure end-to-end encryption (E2EE) but more importantly, the company that runs Signal is a non-profit group. What it means is there’s entirely zero reason to harvest user data. They’ve been so successful that Google and Meta have implemented their own version of the tech infra created by Signal’s engineers.
Trailing behind Signal are Telegram and WhatsApp.
Telegram has good, even top-tier E2EE, but only if you use their Secret Chat option. Otherwise, it means that service stores can access your ordinary two-way message or group threads.
At around two billion monthly users, WhatsApp scores high on popularity, but there have been concerns about how user security is now less of a priority to them although their E2EE is still a built-in feature. What it means is that it scores less on the probability it will sell your data to the highest bidder.
I like both and use both, at the moment. Telegram has this ease of enabling creating community messaging threads as well as disappearing messages a la the “This message will self-destruct in…” alert in Mission Impossible. WhatsApp meantime has an absurdly wide market penetration that I use to communicate with friends in countries like Canada, Hong Kong, the UK, Thailand, and even Myanmar.
From my own user experience, Telegram has the easiest and most attractively cosmetic navigation to use, but for Southeast Asia, there are far more folks using WhatsApp that I communicate with.
All these apps also have a robust infra feedback mechanism for reporting abuse, enabling of rolling screenshots for documentation, and a very transparent user agreement policy that puts privacy and safety at the forefront.


